
Unlocking Blockchain: A Deep Dive into PoW and PoS Consensus Algorithms
Ever wonder how the world of blockchain makes collective decisions? Jump into our deep-dive on proof-of-work (PoW) and proof-of-stake (PoS) consensus algorithms, and explore the fascinating mechanics and key differences between them.
How can we verify that the record 'A transferred one coin to B' is authentic and that 'A transferred one coin to C' is false? Well, consensus algorithms were crafted precisely to solve this puzzling riddle.
So, you've got a blockchain, all shiny and new, promising decentralized, transparent transactions with airtight security. Sounds like magic, right? But wait, you might be scratching your head, wondering, 'How on earth do these transactions get verified before they're added to the blockchain network?' And voila! Here's where the secret sauce of blockchain operation comes into play — the oh-so-vital, yet often unappreciated, consensus mechanism.
Why Is Blockchain Consensus Important?
Before we go down the rabbit hole of consensus algorithms, let's make sure we're all on the same page with some fundamental concepts. We need to get a grip on what a blockchain is and how it does its magic.
Consider this example: A has a stash of four coins. They send one coin flying towards B and two coins to C, keeping the last coin for themselves. These coin dances are etched on a blockchain, a digital ledger that's like a public diary, allowing anyone to confirm the coin balance of each participant at any time and to follow the history of all transactions on the blockchain.
👉 Drawing a parallel to the traditional banking system, picture a 'data center,' a bit like the big boss, that gets updates from participants, gives them a nod of approval, scribbles them into a 'comprehensive ledger', and then shares this vetted data with other participants (think bank branches). However, if a central entity exists, it has the power to alter information at will, potentially misleading other participants, right?
In simpler terms, a blockchain is a digital ledger that never stops jotting down new data or transactions. It was birthed as a wholly decentralized network, sprawling like a web across thousands of computers.
Provided there's a lively grouping of participants, the blockchain keeps humming along. This means that every participant in the network gets an equal shot at the title — each of them can make new entries with no 'central puppet master' pulling the strings.
Participants in the network are pseudonymous — each can be identified in the throng by their addresses, but these identifiers can't be directly linked to the individual's real-world identity. Participants can freely enter or exit the network as they wish.
In its ideal form, a blockchain, embodying a decentralized system, aims to be a bulwark against censorship and uphold objectivity. But, akin to a Shakespearean saga, our protagonist isn't invincible. Objectivity and resistance to censorship can buckle under certain predicaments, such as a 51% attack, where one entity, in a strategic move, commandeers the majority of the network's mining power.
Circling back to the 'ledger' metaphor, every so often, a new 'row' is appended, encapsulating all the changes (transactions) that have unfolded during this period. This data will subsequently be stored and disseminated among thousands of computers within the blockchain network.
This row is termed a block, from which we derive the term 'blockchain', a chain of blocks.
Given that a blockchain bestows equal and open rights to all participants, a question bubbles up: why should anyone trust the data on a blockchain if there's no 'central validator'? How do we authenticate that the statement 'A sent one coin to B' is true and that 'A sent one coin to C' is false? Consensus algorithms were specifically forged to tackle this conundrum.
The workings of the blockchain participants can be demonstrated with an image below (Pic. 1).
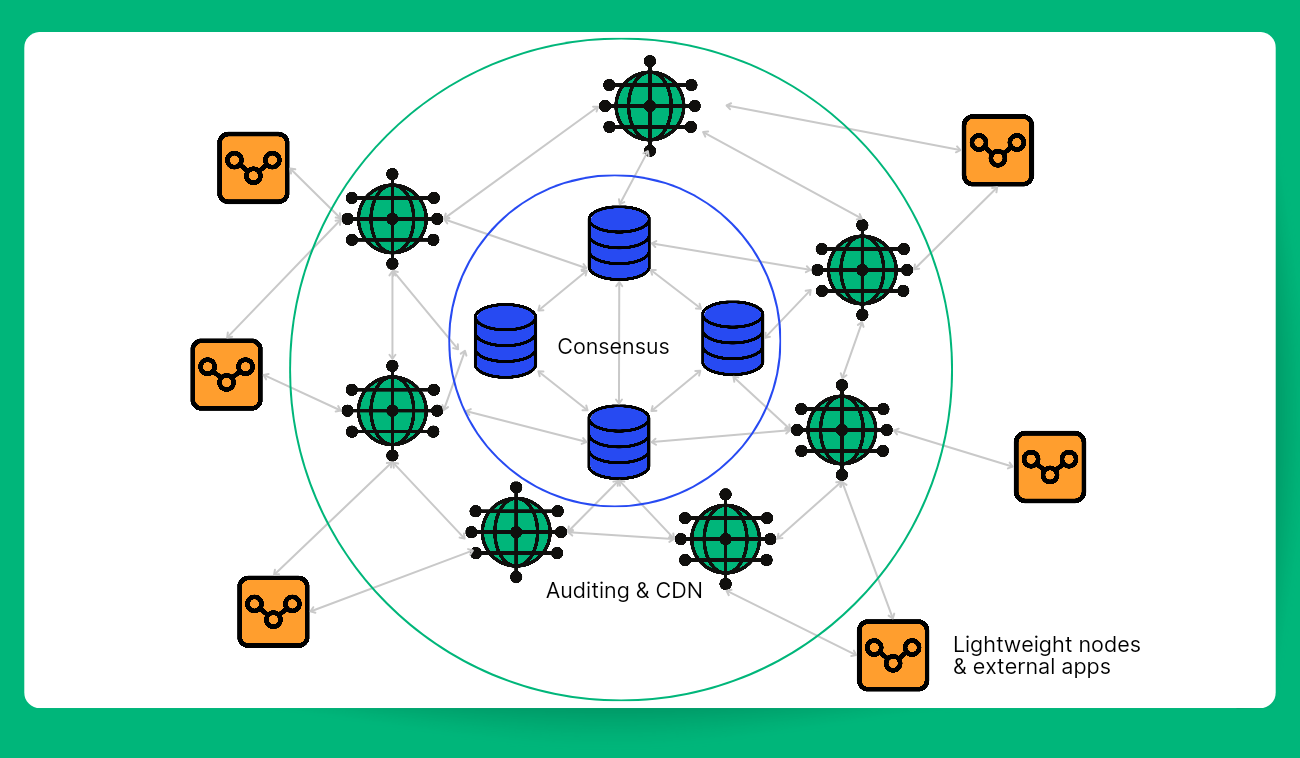
In the given schematic, the blue cylinders symbolize the consensus-building entities that are responsible for making new entries. In a typical blockchain network, this duty is carried out by miners. The green cylinders act as custodians of blockchain copies, authenticating the validity of new records and designating tasks to store the next batch of transactions in blocks. These are generally fully functional wallet nodes. The yellow squares portray the simplest blockchain users, akin to mobile e-wallets, usually having access to records associated only with their own transactions or certain segments of the 'ledger'.
The outcome of applying a cryptographic algorithm to a block's content is a unique electronic signature (also known as a hash), which is used to sign each block (or the new row of the ledger). Any participant in the blockchain can verify and confirm the authenticity of this signature.
Any tampering with the data in the block will lead to a discrepancy in its signature. Moreover, each subsequent signature relies on the previous one, so any participant can confirm whether a new block is a bona fide continuation of the blockchain.
The consensus algorithm plays a pivotal role in ensuring transaction reliability by validating the accuracy of the actions taken. This responsibility is shared among numerous network participants.
There's a variety of consensus algorithms, each flaunting its unique strengths. In this article, we'll take a closer look at two of the most popular ones: proof-of-work and proof-of-stake.
PoW Consensus Algorithm
The proof-of-work (PoW) algorithm is one of the earliest and most prevalent consensus mechanisms used in blockchain networks. It's characterized by its computational complexity, where miners compete to solve intricate mathematical problems.
All transactions are validated through those brain-twisting calculations, the correctness of which can be double-checked by any Tom, Dick, or Harry on the network.
The golden rule? The first miner to untangle the puzzle gets to lord over a new block on the blockchain, engraving the next set of transactions into it. These transactions are then stamped 'confirmed' like a seal of approval.
And what does our victorious miner get, you ask? A shiny reward, of course! A delightful mix of cryptocurrency and transaction fees from the transactions in the new block. A combo that would make any miner’s heart flutter with joy and lure them into this computational rat race.
But wait, there's more! The PoW algorithm packs quite a punch:
- PoW mitigates the risk of network attacks where an adversary spawns a large number of counterfeit participants spewing false information to overpower the majority consensus. To execute such an attack in a PoW-based network would require an astronomical amount of computational power.
- PoW promotes fairness. Each miner's reward is tied to their computational contribution or hash rate. So, if a miner is contributing 2% of the total hash rate, they get to mine an average of 2% of the blocks and receive 2% of the distributed rewards. It's like a 'you reap what you sow' kind of deal.
- Finally, dishonesty comes with a hefty price tag. Miners pour in serious resources (like computational power and electricity) into mining. It's like betting on a high-stakes poker game where the only winning move is to play by the network's rules.
But let's not forget, even PoW has its kryptonite. A 51% attack, where a group controls 51% or more of the network's computational power, can wreak havoc. In such a scenario, the attackers could ignore or alter blocks from other miners and monopolize the mining rewards. But even under these circumstances, the attackers cannot steal bitcoins from users or forge new coins beyond the system's rules.
So there you have it. PoW, with its cocktail of computational challenges and rewards, serves as a sturdy and fair mechanism for transaction validation and block addition in a blockchain network.
PoS Consensus Algorithm
The proof-of-stake (PoS) algorithm bears some similarities to proof-of-work (PoW), but with a significant twist: there's no need for miners to solve complex computational problems. Instead, a different group of participants, known as validators, are at play.
PoS was first brought to life by Peercoin (originally known as PPCoin) in 2012. The driving force behind PoS was to tackle the energy-hungry nature of PoW, offering a more sustainable and eco-friendly alternative.
In the PoS universe, validators are the sheriffs in town, verifying the legitimacy of transactions. To do so, they've got to stake their own coins on the network. Think of it as their skin in the game. These coins are off-limits, locked away in the vault for the duration of the staking period. And if a validator tries any funny business, like approving dodgy transactions, they stand to lose their stake.
Now, you might think that, like in PoW, validators get a pat on the back for solving math problems. Well, you'd be wrong. In the land of PoS, the rewards are a whole different kettle of fish. Some PoS-based cryptocurrencies give validators a cut of the transaction fees as a 'thank you' for their hard work. Others might mint fresh new coins as rewards. The more coins a validator stakes, and sometimes the longer they've staked 'em, the higher their chances of being chosen as the transaction validator and snagging those sweet rewards.
But don't be fooled by the term "votes". In PoS, staked coins aren't casting a ballot in some democratic process. They're more like a financial pledge, a promise from validators that they'll keep the network's integrity intact.
So, that's PoS for you — a world where staked collateral and transaction validation come together to offer a less power-thirsty, yet equally sturdy, mechanism for maintaining a blockchain network.
PoW vs. PoS: Which One Is Better?
Energy consumption
In the world of proof-of-work (PoW), miners have to 'work' hard, crunching numbers with hefty computational resources to secure the network. This high-energy consumption, often seen as wasteful, is a key characteristic of PoW. Why? Because all those computations, while crucial for mining, don't serve any other purpose. On the flip side, proof-of-stake (PoS) takes a nap on the energy consumption front. There are no 'unnecessary' calculations in PoS land, making it the more energy-efficient cousin of PoW.
Scalability
Got a need for speed? You might find blockchain's transaction processing speeds a bit slow, especially when compared to traditional systems. This is the trade-off for security and decentralization. However, when it comes to scalability, PoW isn't the king of the hill. Sharding, a method that can speed up transaction processing, is theoretically possible for any blockchain. But in practice, working sharding models have mainly been seen in the PoS realm.
Decentralization
Both PoW and PoS have their battles with centralization. In PoW, the mining industry dominates, with a handful of big players controlling a major chunk of the computing power (and reaping most of the rewards). Over in PoS, the wealthy users who stake big often stand to win big, leading to a similar centralization concern. However, keep in mind that not all PoS systems are created equal — some use various methods like randomization to level the playing field.
Safety
Safety first, right? Every blockchain network's priority is security. The infamous '51% attack' is a potential threat in both PoW and PoS systems. In PoW, an attacker would need to command more than half of the mining power (which requires astronomical computational resources). In PoS, they'd need to control over half of the staked coins. But here's the kicker: in PoS, an attacker with such a large stake would have a significant financial incentive to keep the network secure, as their own wealth would be at risk if they compromised the network's integrity.
Bottom Line
In conclusion, PoW and PoS are two sides of the same coin, each with its own strengths and weaknesses. The 'better' choice hinges on the specific use case, goals, and network design. Both offer unique solutions to the challenges of securing a decentralized network, and the choice between the two is not a one-size-fits-all answer.
Got Some Trading Time?
If you've been on the hunt for a trustworthy crypto trading platform or a variety of profitable crypto trading bots, your search ends at Bitsgap!
With Bitsgap, you can connect all your exchange accounts and manage trades from one comprehensive interface, packed with intelligent trading tools and automated crypto bots crafted to capitalize on any market.
Feel free to pick from our successful default strategies, or tailor your own strategy — whether it's DCA, BTD, COMBO, or GRID — to perfectly suit your trading style.
Give Bitsgap a try, you'll wonder why you didn't start sooner!
FAQs
What Is Blockchain Consensus?
Blockchain consensus plays a pivotal role in blockchain technology, functioning as a means for all network participants (or nodes) to agree on the authenticity of transactions. This consensus process ensures that every transaction added to the blockchain is universally accepted as the sole truth by all nodes, thwarting double-spending and fraudulent activities.
Consider the consensus mechanism as a set of rules that all nodes in the network use as a guideline to verify information. It's the way all members of a blockchain network come to a mutual understanding about the current status of the shared ledger. Thus, consensus algorithms are essential in upholding the integrity and security of a blockchain network.
What Consensus Algorithms Are There?
Consensus algorithms are the rule sets that guide nodes in a blockchain network to reach an agreement on the information being recorded to the ledger. There exists a variety of consensus algorithms, each carrying its own set of pros and cons. Some of the most prevalent ones include proof-of-work, proof-of-stake, delegated proof-of-stake, proof-of-authority, and Byzantine Fault Tolerance (BFT), along with its alterations like PBFT and dBFT.
