
Understanding Zero Knowledge Proofs and Their Importance
Imagine a world where you can prove something is true without revealing any details—this is the magic of Zero-Knowledge Proofs (ZKPs). From safeguarding privacy to scaling blockchains, ZKPs are revolutionizing how we think about security and decentralization.
Zero-knowledge proofs (ZKPs) are a fascinating cryptographic technique that allows one party (the prover) to convince another party (the verifier) that a statement is true, without revealing any information beyond the validity of the statement itself. Imagine being able to prove you know a secret password without actually typing it in, or demonstrating you have enough funds for a transaction without disclosing your balance. This seemingly paradoxical ability is what makes ZKPs so powerful and relevant in today's privacy-conscious world.
👉 In this article, we'll delve into the world of zero-knowledge proofs, exploring how they work, their various types and applications, the benefits they offer, and the limitations they face.
What Are Zero Knowledge Proofs in Blockchain
Zero Knowledge Proofs (ZKPs) are cryptographic methods that allow one party (the prover) to prove to another party (the verifier) that a specific statement is true without revealing any additional information beyond the validity of the claim. In the context of blockchain, ZKPs are particularly valuable because they enable secure and private transactions without exposing sensitive data.
Blockchain networks are inherently transparent, which can be both an advantage and a limitation. While transparency ensures trust and accountability, it also risks exposing personal or sensitive information. ZKPs address this challenge by enabling privacy-preserving features on blockchain systems. For example, they can verify that a transaction is valid (e.g., the sender has sufficient funds) without revealing the transaction amount or the identities of the parties involved.
👉 This makes ZKPs a cornerstone of privacy-focused blockchain protocols like Zcash and enhances scalability by reducing the amount of data stored on-chain. As blockchain adoption grows across industries, ZKPs are playing a critical role in balancing transparency with privacy and efficiency.
Who Invented Zero Knowledge Proofs
Zero Knowledge Proofs were first introduced in 1985 by three computer scientists: Shafi Goldwasser, Silvio Micali, and Charles Rackoff. Their groundbreaking paper titled “The Knowledge Complexity of Interactive Proof Systems” laid the theoretical foundation for ZKPs.
Their work introduced the concept of proving the validity of a statement without revealing the underlying information and established the principles of “knowledge complexity,” which measures the amount of knowledge transferred during a proof. This innovation was a major milestone in cryptography and earned Goldwasser and Micali the Turing Award in 2012, often referred to as the "Nobel Prize of Computing."
👉 Over the years, this theoretical concept has evolved into practical tools and applications, particularly with the rise of blockchain technology, where ZKPs have become a key component for enabling privacy-preserving and scalable systems.
How Do Zero Knowledge Proofs Work?
Zero Knowledge Proofs work by enabling a prover to demonstrate the truth of a statement to a verifier without disclosing any information about the statement itself. This process generally follows three core principles:
- Completeness: If the statement is true, the verifier will be convinced by the proof.
- Soundness: If the statement is false, the verifier cannot be fooled into believing it is true.
- Zero Knowledge: The verifier learns nothing beyond the fact that the statement is true.
There are two main types of ZKPs based on how the interaction occurs between the prover and the verifier:
- Interactive ZKPs: The prover and verifier engage in a series of exchanges, where the verifier poses challenges, and the prover responds to demonstrate the truth of the statement.
- Non-Interactive ZKPs: The proof is generated once by the prover and can be verified without additional interaction.
In blockchain, non-interactive ZKPs, such as zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge), are widely used because they are efficient and scalable. These proofs rely on advanced mathematical techniques like elliptic curve cryptography and polynomial commitments to prove validity without requiring back-and-forth communication.
Types of Zero Knowledge Proofs
Zero-knowledge proofs come in several forms, each with unique characteristics and use cases:
1. zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge):
- Succinct: zk-SNARK proofs are very small, making them efficient to verify.
- Non-Interactive: They require only a single message from the prover to the verifier, unlike interactive proofs.
- Arguments of Knowledge: They demonstrate that the prover possesses certain knowledge (e.g., the solution to a problem) without revealing the knowledge itself.
- Trusted Setup: A key drawback is the need for a trusted setup phase, where secret parameters are generated. If these parameters are compromised, the security of the system could be at risk. This setup is typically done using multi-party computation (MPC) ceremonies to minimize the risk.
- Use Cases: Widely used in privacy-focused cryptocurrencies like Zcash and for verifying computations off-chain in zk-Rollups.
2. zk-STARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge):
- Scalable: zk-STARKs offer better scalability than zk-SNARKs, especially for very large computations. Proof generation time increases more slowly with the complexity of the statement being proven.
- Transparent: They eliminate the need for a trusted setup, making them more secure and resistant to potential parameter manipulation. This transparency comes from relying on collision-resistant hash functions instead of elliptic curve pairings.
- Larger Proof Sizes: zk-STARK proofs are generally larger than zk-SNARK proofs, which can be a disadvantage in some applications.
- Post-Quantum Security: zk-STARKs are considered more resistant to attacks from quantum computers compared to zk-SNARKs.
- Use Cases: Suitable for scaling solutions like StarkNet and for applications where transparency and post-quantum security are paramount.
3. Bulletproofs:
- Short Proofs: Bulletproofs are designed for range proofs, proving that a value falls within a specific range without revealing the exact value. They offer relatively short proof sizes.
- No Trusted Setup: Like zk-STARKs, they don't require a trusted setup.
- Use Cases: Used in confidential transactions and for proving solvency without revealing specific balances. Monero uses a variant of Bulletproofs.
4. Sigma Protocols:
- Interactive: Sigma protocols require multiple rounds of interaction between the prover and the verifier.
- Simpler Construction: They are generally simpler to understand and implement compared to zk-SNARKs and zk-STARKs.
- Less Practical for Blockchain: Their interactive nature makes them less suitable for most blockchain applications, which require non-interactive proofs.
- Building Blocks: While not directly used in many blockchains, they serve as building blocks for more complex ZKP constructions. For example, they can be made non-interactive using the Fiat-Shamir heuristic.
5. PLONK (Permutations over Lagrange-bases for Oecumenical Noninteractive arguments of Knowledge):
- Universal and Updateable Trusted Setup: PLONK uses a universal trusted setup, meaning a single setup can be used for multiple different circuits. This setup can also be updated, further enhancing security.
- Efficient: PLONK offers competitive proof sizes and verification times.
- Growing Popularity: Gaining traction as a versatile ZKP system.
👉 Each type of ZKP has trade-offs in terms of efficiency, scalability, and trust assumptions, making them suitable for different use cases.
Zero Knowledge Proofs Example
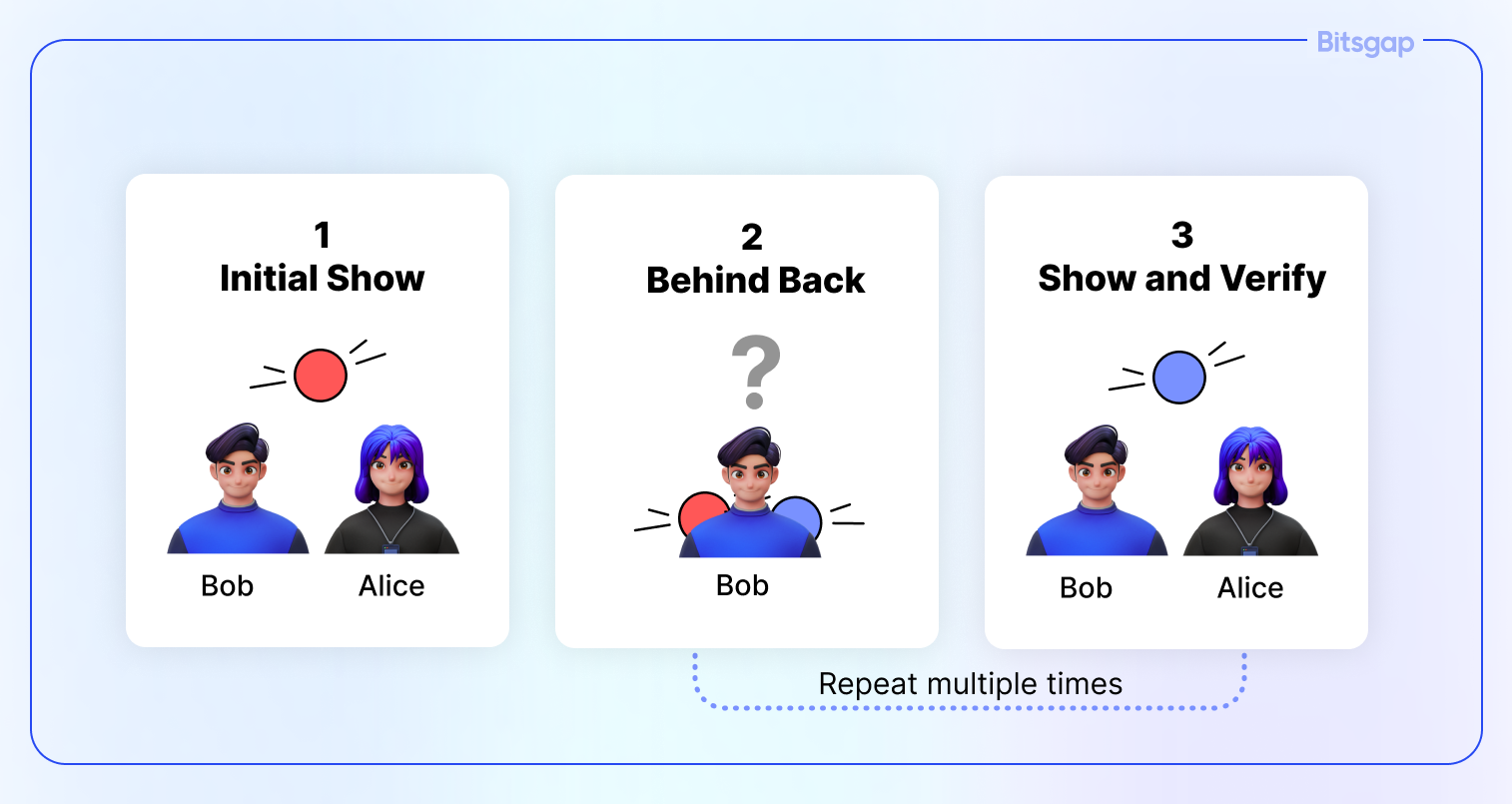
To understand ZKPs better, consider a classic example of a colorblind friend:
Imagine Alice wants to prove to Bob, who is colorblind, that two balls (red and blue) are of different colors, without revealing which ball is which.
- Bob puts both balls behind his back and shows one ball to Alice.
- Bob then asks Alice whether he switched the ball or kept the same one.
- Since Alice can see the colors, she always answers correctly.
If this process is repeated multiple times and Alice consistently answers correctly, Bob becomes convinced that the balls are indeed of different colors, even though he doesn’t know which is red and which is blue.
This analogy showcases the essence of ZKPs: proving the truth of a claim without revealing any additional information.
Benefits and Challenges of Zero Knowledge Proofs and Protocols in Blockchain
Zero-knowledge proofs offer significant advantages for blockchain technology, but they also face certain limitations. Ongoing research and development are actively addressing these challenges, making ZKPs increasingly practical for widespread adoption.
Benefits:
- Enhanced Privacy: ZKPs enable confidential transactions and protect sensitive data, such as identity attributes, by allowing users to prove statements without revealing the underlying information.
- Improved Scalability: ZKPs are key to Layer-2 scaling solutions like zk-Rollups, enabling significantly higher transaction throughput by verifying bundles of transactions off-chain.
- Security: ZKPs enhance security by preventing double-spending and other fraudulent activities, and they minimize the risk of data breaches by reducing the amount of information exposed.
- Trustless Verification: ZKPs allow anyone to verify the validity of a statement without needing to trust the prover or any third party, a cornerstone of decentralized systems.
- Interoperability: ZKPs can facilitate secure and trustless communication and data verification between different blockchains.
- Compliance: ZKPs support selective disclosure, allowing users to reveal specific information to authorized parties while maintaining overall privacy, which can be crucial for regulatory compliance.
Challenges:
- Computational Overhead: Generating ZKPs can be computationally intensive, particularly for complex statements, posing challenges for resource-constrained devices. However, ongoing research is improving the efficiency of proof generation.
- Trusted Setup (for some types): Some ZKP systems, like zk-SNARKs, require a trusted setup phase, which can be a security vulnerability if compromised. Newer systems like zk-STARKs and Bulletproofs address this by eliminating the need for a trusted setup.
- Complexity: The underlying cryptographic principles and mathematics of ZKPs can be complex, making implementation and understanding challenging. Fortunately, developer tools and libraries are simplifying this process.
- Proof Size (for some types): zk-STARK proofs can be significantly larger than zk-SNARK proofs, requiring more storage and bandwidth.
- Prover Time: Generating a proof can take a considerable amount of time, potentially impacting user experience in some applications.
- Quantum Resistance: While some ZKPs are quantum-resistant, others based on elliptic curve cryptography might be vulnerable to future quantum computers.
- General-Purpose vs. Application-Specific: Choosing the right ZKP system depends on the specific application, as some are optimized for particular types of statements (e.g., range proofs).
👉 Despite these challenges, ongoing research and development are addressing these limitations, making ZKPs more practical for widespread use.
Applications of Zero Knowledge Proofs
Zero-knowledge proofs (ZKPs) have a wide range of applications across various industries, offering innovative solutions for privacy, security, and scalability:
- Blockchain and Cryptocurrencies:
- Privacy-Preserving Transactions: Cryptocurrencies like Zcash, Monero, and Secret Network use ZKPs (zk-SNARKs, Bulletproofs, etc.) to shield transaction details like sender, recipient, and amount, enhancing user privacy and fungibility.
- Layer-2 Scaling Solutions: zk-Rollups (e.g., StarkNet, zkSync) leverage ZKPs to bundle thousands of transactions off-chain and verify them on-chain with a single proof, drastically improving transaction throughput and reducing costs. Validium is another ZKP-based scaling solution but with data availability off-chain.
- Identity Management: Decentralized identity systems can use ZKPs to allow users to selectively disclose verified credentials (e.g., age, nationality) without revealing their entire identity.
- Tokenized Assets: ZKPs can be used to represent and trade tokenized assets (e.g., stocks, bonds) while preserving the privacy of ownership and transaction details.
- Decentralized Finance (DeFi): ZKPs can enhance privacy in DeFi protocols, allowing users to participate in lending, borrowing, and other financial activities without revealing their financial positions.
- Authentication Systems:
- Passwordless Authentication: ZKPs enable users to prove knowledge of a secret (e.g., a private key) without revealing the secret itself, eliminating the need for passwords.
- Biometric Authentication: ZKPs can be used to authenticate users based on biometric data (e.g., fingerprints) without storing or transmitting the raw biometric data.
- Secure Voting Systems:
- Verifiable Elections: ZKPs can ensure the integrity of elections by allowing voters to verify that their votes were counted correctly without revealing their individual votes. They can also prevent double voting.
- Anonymous Voting: ZKPs can provide anonymity for voters while still ensuring the verifiability of the election outcome.
- Identity Verification:
- Privacy-Preserving KYC/AML: ZKPs enable users to prove their identity and meet Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements without disclosing unnecessary personal information.
- Age Verification: Users can prove they are of legal age without revealing their exact date of birth.
- Supply Chain Management:
- Provenance Tracking: ZKPs can be used to track the origin and movement of goods through a supply chain, verifying authenticity and preventing counterfeiting without revealing sensitive supply chain details.
- Compliance Verification: Companies can use ZKPs to prove compliance with regulations (e.g., environmental standards) without disclosing proprietary information.
- Healthcare:
- Selective Medical Data Sharing: Patients can share specific medical information with healthcare providers or researchers without revealing their entire medical history.
- Insurance Claims: Patients can prove eligibility for insurance claims without disclosing unnecessary medical details.
- IoT and Secure Communication:
- Device Authentication: ZKPs can be used to authenticate IoT devices and establish secure communication channels without revealing sensitive device information.
- Data Integrity: ZKPs can ensure the integrity of data transmitted between IoT devices, preventing tampering and ensuring data authenticity.
- Gaming:
- Fairness and Transparency: ZKPs can be used to prove the fairness of online games and ensure that the game operates according to its stated rules without revealing the game's internal logic.
- True Randomness: ZKPs can be used to generate verifiable random numbers, ensuring fairness in games and other applications that rely on randomness.
👉 As ZKP technology continues to mature and research progresses, its potential to revolutionize privacy, security, and scalability across various industries will only continue to expand. We can expect to see even more innovative applications emerge in the coming years.
Key Blockchain Projects Using Zero Knowledge Proofs
Let’s take a closer look at how some projects are integrating ZKPs into their protocols to redefine privacy, scalability, and efficiency in their respective domains. Each project showcases a unique implementation of ZKPs, tailored to its goals and use cases, offering insights into the profound impact of this technology on the future of decentralized systems.
1. Zcash (ZEC):
Zcash stands out as a privacy pioneer in the cryptocurrency world. It was among the first to leverage the power of zk-SNARKs, a cryptographic tool that allows for "shielded transactions." These transactions effectively encrypt all key information – the sender, the recipient, and the amount being transferred – ensuring a high level of confidentiality. Furthermore, Zcash offers a feature called selective disclosure. This allows users to prove specific details about a transaction to a third party, like an auditor, without revealing their entire transaction history, offering a crucial balance between privacy and accountability.
2. Ethereum (ETH) and zk-Rollups:
Ethereum's scalability roadmap heavily relies on zk-Rollups, a Layer 2 scaling solution that plays a pivotal role in improving the network's efficiency. zk-Rollups execute transactions off-chain, bundle them together, and submit a single, concise validity proof to the Ethereum mainnet. This process significantly reduces gas costs and increases transaction throughput while maintaining the same level of security as the Ethereum base layer.
Several key projects are driving zk-Rollup adoption:
- zkSync is one of the most popular zk-Rollup solutions. It provides two main offerings:
- zkSync Era, its mainnet solution, focuses on general-purpose smart contracts and scalability while providing user-friendly developer tools.
- zkSync Lite (formerly zkSync 1.0) is a cost-optimized version designed for token transfers and payments, making it an accessible option for those prioritizing low transaction costs. zkSync is known for its emphasis on a seamless developer experience to encourage adoption.
- StarkNet sets itself apart by using zk-STARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge) instead of zk-SNARKs. zk-STARKs eliminate the need for a trusted setup, offering greater transparency and stronger resistance to potential threats from quantum computers. StarkNet focuses on general-purpose computation and supports smart contracts written in Cairo, a programming language specifically designed for STARK-based systems. This makes StarkNet versatile for decentralized applications that require advanced computation.
- Scroll places a strong emphasis on EVM equivalence, ensuring seamless compatibility with the Ethereum Virtual Machine. This simplifies the process of migrating existing Ethereum decentralized applications (dApps) by allowing developers to use the same tools and codebases with minimal adjustments. Scroll aims to provide a smooth transition to Layer 2 for Ethereum developers.
- Polygon zkEVM is another prominent zk-Rollup project striving for EVM equivalence. Like Scroll, Polygon zkEVM allows Ethereum dApps and smart contracts to operate seamlessly on its platform without requiring significant changes to the code. This approach aligns with Ethereum’s long-term goal of creating a scalable, unified ecosystem while preserving the developer experience.
By leveraging zk-Rollups, Ethereum is addressing its scalability challenges while laying the groundwork for a more efficient and user-friendly blockchain ecosystem. Each of these projects contributes unique innovations to the zk-Rollup space, making it a cornerstone of Ethereum's future scalability efforts.
3. Polygon (MATIC):
Polygon (MATIC) is pursuing a comprehensive approach to scaling Ethereum, leveraging multiple Layer 2 solutions. These include zk-Rollups, such as Polygon zkEVM and Polygon Miden, as well as optimistic rollups. Polygon zkEVM is designed to provide developers with an environment that feels familiar to Ethereum, offering full EVM equivalence. This allows developers to seamlessly migrate their decentralized applications (dApps) without modifying existing code, fostering growth and adoption within the Polygon ecosystem. Meanwhile, Polygon Miden uses zk-STARKs to enable scalable and private computation, further diversifying Polygon’s offerings. By exploring both zk-Rollups and optimistic rollups, Polygon is solidifying its position as a leader in Ethereum scaling solutions.
4. Mina Protocol:
Mina Protocol uses recursive zk-SNARKs to maintain a remarkably small and constant blockchain size, which is one of its defining features. Unlike traditional blockchains that grow larger over time as new transactions are added—requiring increasing amounts of storage and processing power—Mina compresses its entire blockchain history into a single, compact cryptographic proof. This proof, which remains roughly the size of a few tweets, represents the entire state of the blockchain and can be easily verified by any participant.
The use of recursive zk-SNARKs enables Mina to continually compress new blocks into this single proof, ensuring that the blockchain size stays constant regardless of network growth. This innovation allows even low-powered devices, such as smartphones, to quickly sync with the network and participate as full nodes. By reducing hardware requirements, Mina fosters greater accessibility and decentralization, making it significantly more inclusive than traditional blockchain systems. This constant and minimal blockchain size sets Mina apart as one of the most lightweight and scalable blockchain projects in the space.
5. Aztec Network:
Aztec Network is focused on enhancing privacy within the Ethereum ecosystem, with a particular emphasis on smart contracts. The network provides a dedicated infrastructure for privacy-preserving decentralized finance (DeFi) applications, enabling users to engage in blockchain activities while keeping their sensitive data confidential.
Aztec achieves this through its use of zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge), a cryptographic technology that ensures transactional privacy by allowing proofs of correctness without revealing underlying data. This innovative approach allows developers to build decentralized applications (dApps) that leverage the transparency and security of Ethereum while safeguarding user information.
Aztec's focus on programmable privacy empowers developers to integrate privacy features directly into their smart contracts. This opens up new possibilities for creating secure and confidential dApps, such as private DeFi protocols, identity management systems, and more. By combining Ethereum's programmability with advanced cryptographic privacy, Aztec Network is paving the way for a more secure and user-centric blockchain ecosystem.
6. Horizen (ZEN):
Horizen (ZEN) is a blockchain platform that extends beyond a single chain by enabling the creation of sidechains. These sidechains are independent, customizable blockchains designed to meet the specific needs of various applications, providing a flexible and adaptable environment for developers.
Horizen's sidechain architecture leverages zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) to deliver both privacy and scalability. The use of zk-SNARKs ensures that transactions occurring on these sidechains can remain private, protecting sensitive data while maintaining transparency where necessary.
In addition to privacy, Horizen's sidechains benefit from the robust security of the main Horizen blockchain, which acts as the base layer. The platform also emphasizes interoperability, allowing sidechains to interact seamlessly with the main Horizen chain and with each other. This combination of privacy, scalability, and interoperability makes Horizen an attractive solution for projects requiring customized blockchain implementations, such as enterprise applications, DeFi platforms, and data privacy solutions.
7. Filecoin (FIL):
Filecoin (FIL) leverages zk-SNARKs in an innovative way to verify data storage within its decentralized storage network. These cryptographic proofs are integral to Filecoin's consensus mechanisms, specifically Proof of Replication (PoRep) and Proof of Spacetime (PoSt).
- Proof of Replication (PoRep): PoRep ensures that storage providers have genuinely stored unique, complete copies of the data they claim to hold. This prevents fraudulent behavior, such as pretending to store data without actually doing so, while also guaranteeing redundancy across the network.
- Proof of Spacetime (PoSt): PoSt verifies that storage providers are continuously storing the data over a specified period of time. This ensures ongoing reliability and that the data remains accessible when needed.
The use of zk-SNARKs in these proofs is crucial for maintaining privacy and data confidentiality. zk-SNARKs allow the generation and verification of these proofs without exposing the actual content of the stored data. This ensures that sensitive user information remains private while still allowing the system to validate storage integrity and reliability.
By combining zk-SNARKs with its decentralized storage model, Filecoin achieves a secure, private, and trustless framework for verifying data storage, making it a cornerstone of the Web3 infrastructure.
8. Aleo:
Aleo is a blockchain platform uniquely designed for building privacy-preserving applications. It combines the power of zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) with a purpose-built programming language called Leo to provide a robust foundation for private, decentralized applications.
- zk-SNARKs: Aleo uses zk-SNARKs as its cryptographic backbone, enabling developers to create applications where sensitive user data remains confidential. These zero-knowledge proofs allow computations to be verified without revealing the underlying data, ensuring both privacy and security.
- Leo Programming Language: Leo is a developer-friendly, domain-specific programming language designed to simplify the creation of privacy-focused applications. By abstracting the complexities of zero-knowledge cryptography, Leo empowers developers to build private applications more efficiently and effectively.
This combination allows Aleo to support fully private applications where data confidentiality is maintained even during processing on the blockchain. Aleo's emphasis on programmable privacy and user-centric data security positions it as a standout platform in the blockchain space, catering to use cases that prioritize privacy by default.
9. Secret Network (SCRT):
Secret Network (SCRT) is a blockchain platform that prioritizes privacy in smart contracts through its innovative "Secret Contracts." These contracts enable private computation and data storage, ensuring that sensitive information remains confidential throughout the contract's lifecycle.
Secret Contracts utilize a specialized implementation of zk-SNARKs alongside secure hardware-based Trusted Execution Environments (TEEs) to achieve privacy. This approach ensures that data within these contracts stays encrypted and is only accessible to authorized parties, even during the execution of the contract.
By enabling selective disclosure of information, Secret Network allows for secure and confidential transactions and computations on the blockchain. This opens up new possibilities for privacy-preserving decentralized applications (dApps) across various fields, such as private DeFi, healthcare, and identity management. Secret Network's focus on programmable privacy makes it a unique and essential player in the blockchain ecosystem, addressing the growing demand for data confidentiality in decentralized systems.
10. Loopring:
Loopring provides an innovative solution for decentralized exchanges (DEXs) by utilizing a zk-Rollup architecture built on an order book model. This design combines the scalability of off-chain processing with the security and decentralization of Ethereum, enabling fast, low-cost, and private trading.
- zk-Rollups: Loopring leverages zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) within its zk-Rollup framework to aggregate and process thousands of transactions off-chain. These transactions are then bundled into a single cryptographic proof, which is verified on-chain. This approach drastically reduces gas costs and increases throughput while maintaining Ethereum-level security.
- Privacy and Efficiency: By using zk-SNARKs, Loopring ensures that sensitive transaction data remains private during off-chain processing. At the same time, the integrity of these transactions is cryptographically verified when they are submitted to the Ethereum blockchain.
Loopring’s architecture enables DEXs to achieve high performance similar to centralized exchanges while preserving the security, privacy, and self-custody benefits of decentralized trading. This makes Loopring a pioneering solution in the development of scalable and efficient decentralized finance (DeFi) applications.
Conclusion
Zero-Knowledge Proofs (ZKPs) are a revolutionary cryptographic innovation that allows one party to prove the truth of a statement to another without revealing any underlying data. This concept, particularly through implementations like zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge), has become a transformative force in blockchain technology. By enabling secure, private, and efficient verification processes, ZKPs address some of the most pressing challenges in the blockchain space, such as scalability, privacy, and data confidentiality.
In the blockchain ecosystem, ZKPs work by ensuring that sensitive information remains hidden while still being cryptographically verified. This makes them a cornerstone for applications that require both privacy and trust, including private transactions, decentralized computation, and off-chain scalability solutions. Their impact is far-reaching, enabling blockchain networks to achieve a unique balance between transparency and confidentiality, which is critical for the success of decentralized systems.
Despite their many benefits, ZKPs are not without their challenges. The technology can be resource-intensive, requiring significant computational power to generate proofs. Additionally, developing ZKP-based systems often demands specialized expertise, which can act as a barrier to widespread adoption. However, with continuous advancements and growing interest in zero-knowledge cryptography, these limitations are gradually being addressed, making the technology more accessible and practical over time.
For those looking to engage with the cryptocurrency ecosystem, cryptocurrency trading platforms like Bitsgap offer an excellent way to optimize your trading experience. Bitsgap connects to 15 major exchanges, giving you access to a wide range of cryptocurrencies in one place. The platform’s advanced features, such as trading automations, smart orders, and portfolio management tools, make it an ideal choice for both beginners and experienced traders. Whether you're trading tokens backed by zero-knowledge technology or exploring other blockchain projects, Bitsgap provides the tools and flexibility to amplify your returns and navigate the market with ease.
